CVE-2023-30094
In this post I will go through CVE-2023-30094: the description, replication of the vulnerability and PoC.
Flow, a TotalJS product, is
"It's a friendly, modern, straightforward Visual Programming Interface for Low-code Development accessible through a web browser.
The tool integrates processes, and transforms various events and data in real time."
Description of the vulnerability
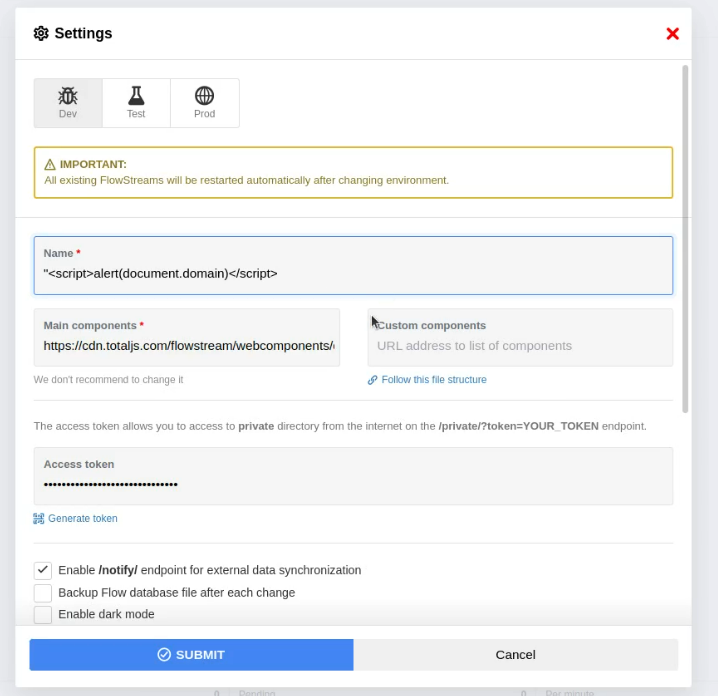
The version 10 of Flow contains a vulnerable XSS page. The software does not sanitize the name input field of the page.
Replication of the vulnerability
- Login in the application.
- Click on settings.
- Set
"><img src=x onerror=alert(document.domain)>as platform name and save. - Logout and XSS will fire.