CVE-2023-27070
In this post I will go through CVE-2023-27070: the description, replication of the vulnerability and PoC.
openplatform is an Open-Source JavaScript based “beautiful and simple portal for running, integrating and managing multiple 3rd party web applications” (link to the GitHub repo).
From the GitHub description we can read:
"OpenPlatform is a stylish and straightforward Web OS platform / Portal for running, integrating, and managing multiple 3rd party web applications.
OpenPlatform provides running applications with a set of services, such as user and security management or notifications,
so that programmers can focus on business logic.
OpenPlatform is an enterprise-ready solution".
Among its benefits they list:
- Container for 3rd party apps
- Supports user groups and permissions
- Supports notifications, and sounds
- Powerful user management
- Fully optimized for mobile devices
- and many more…

Description of the vulnerability
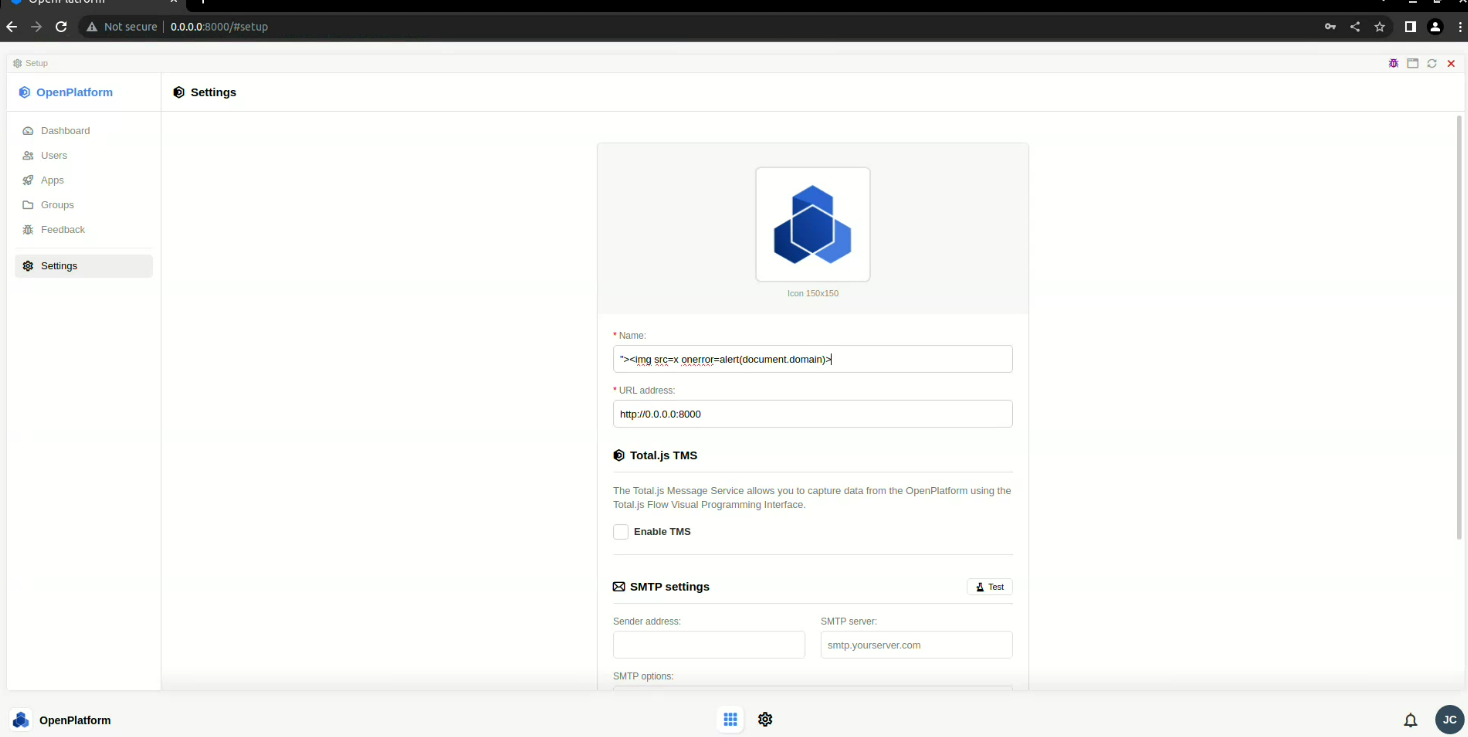
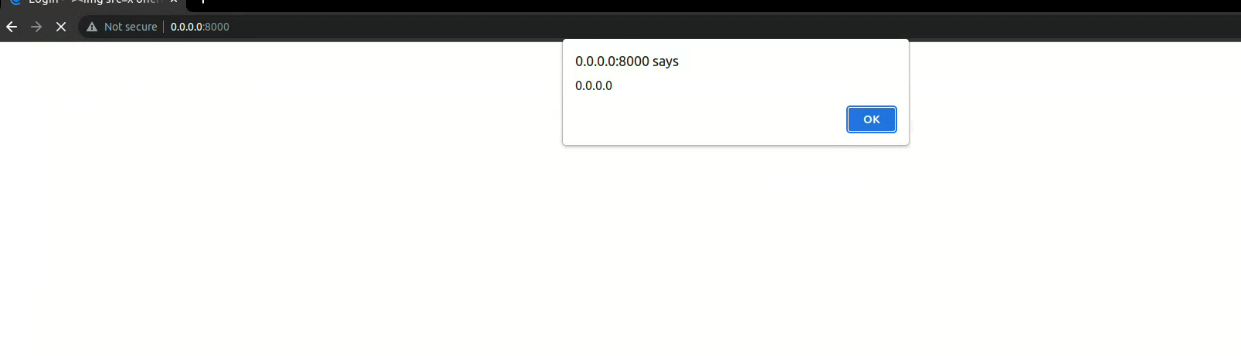
The account name is not properly sanitized and can execute JavaScript code when reflected in the website. I’ve opened an issue in GitHub issue tracker (https://github.com/totaljs/openplatform/issues/53).
Replication of the vulnerability
- Login in the application.
- Click on setup
- Click My settings
- Set
"><img src=x onerror=alert(document.domain)>as platform name and save. - Logout and XSS will fire.