CVE-2022-41392
In this post I will go through CVE-2022-41392: the description, replication of the vulnerability and PoC.
This is my first 0day :)
TotalJS is an Open-Source JavaScript platform providing a lot of FOSS tools and libraries written in Javascript/NodeJS. This vulnerability affects the TotalJS CMS product (link to the GitHub repo).
From the Official CMS website we can read:
"Get a simple, clean, beautiful, and design-driven Total.js Content Management System with a lot of impressive features.
Total.js CMS helps you manage your new fascinating commercial or personal websites easily.
Node.js CMS is built on NoSQL embedded database and with no dependencies [...]".
Description of the vulnerability
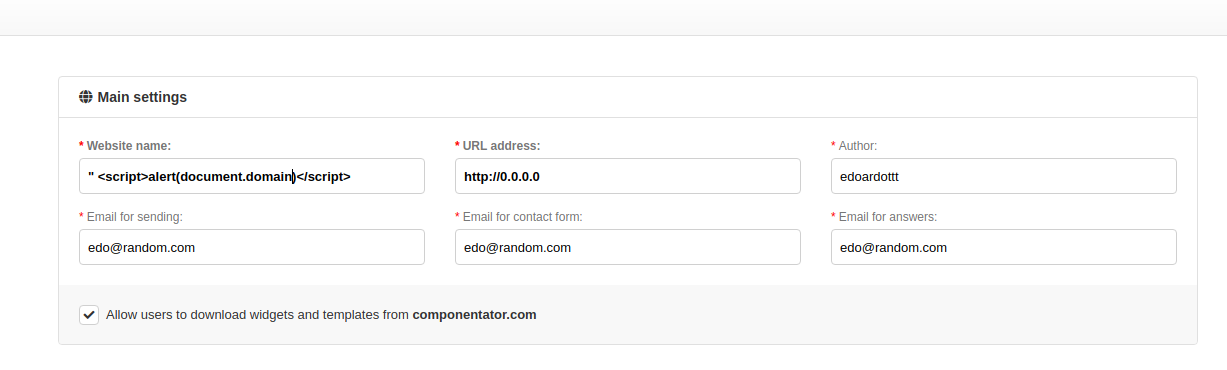
A cross-site scripting (XSS) vulnerability in TotalJS commit 8c2c8909 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Website name text field under Main Settings.
This is the vulnerable code:
<head>
<title>@{'%name'} v@{'%version'}</title>
<meta charset="utf-8" />
<meta http-equiv="X-UA-Compatible" content="IE=10" />
<meta name="format-detection" content="telephone=no" />
<meta name="viewport" content="width=device-width, initial-scale=1, user-scalable=no" />
<meta name="robots" content="all,follow" />
The name parameter in file views/admin.html is directly inserted in the response without being properly sanitized.
Replication of the vulnerability
- Log in to the application.
- Set
" <script>alert(document.domain)</script>as website name. - Fill in other required fields with random values and save.
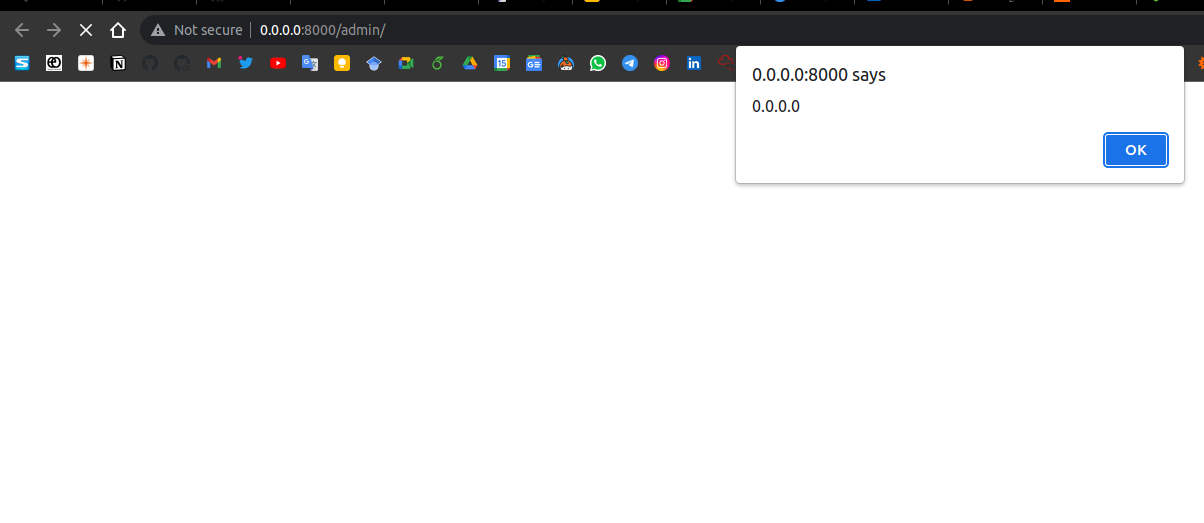
- Then just visit the admin dashboard and the alert will fire.
Each time a target will visit the dashboard the payload will fire, even if the target is not logged in!
Since the website redirects to /admin/ presenting the login form, the payload is reflected also there.
To test this, just click logout and reload the page.